Gerald Combs
My first real networking job in the IT department of a university in the early ’90s. We had all sorts of different computers, from room-sized VAXes to workstations and PCs to specialized hardware which needed to be connected to each other and to other universities. Part of my job was to help make the network reliable, and to do that I used a Sniffer™️, a protocol analyzer made by Network General. It was my first exposure to protocol analysis and set me on a path which led to Wireshark.
Over the next few years, two things happened which shaped the world of protocol analysis and software development in general. First, off-the-shelf hardware became much more powerful and much more capable. Because of that you had less of a need for specialized hardware to capture network packets.
During the same time period the internet grew large, fast, and reliable enough (thanks in part to The Sniffer) to allow large-scale distributed collaboration. This had a profound and enduring effect on how software was developed — you were no longer limited to a few people sitting together in the same room. You could instead develop software in a distributed fashion with people working on the same code around the world, and this resulted in a wave of open source software projects such as the Linux kernel, the Apache Web server, the VLC video player, and Wireshark.
In the late 1990s I was working at a small ISP. We didn’t have the budget for a Sniffer, but we did have problems with our network. I needed a protocol analyzer that ran on Linux and Solaris, and ended up writing one, which ultimately became Wireshark. Thanks to contributions from thousands of developers, Wireshark has grown to become a powerful network protocol analyzer which is used by millions of people around the world to learn about networks and to make them fast, reliable, and secure.
So, what does Wireshark do, exactly? Suppose we have a network packet, which might look like this:
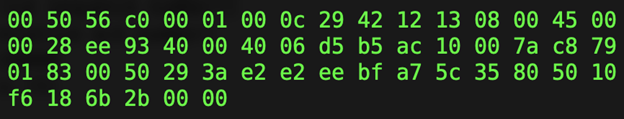
The different numbers in different places determine how the packet moves across the network and what happens when the recipient receives the packet.
Wireshark uses a process called dissection to break the packet up into its constituent fields and extracts as much information as it can from each field. It displays these fields in a format that humans can work with so that we can analyze and troubleshoot networks.
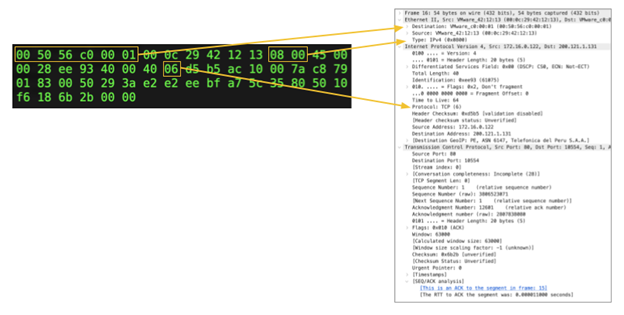
Wireshark can not only show fields for data contained in the packet, it can show information from external sources or inferred from other packets, such as host names, geolocation information, delta times, and more. It also uses fields to provide an array of powerful analysis features. You can use them to create filters to drill down to the traffic you’re interested in, draw graphs, colorize Wireshark’s output, and more.
Most of the time you’re dealing with many packets, and Wireshark’s main window displays them as a selectable list at the top.
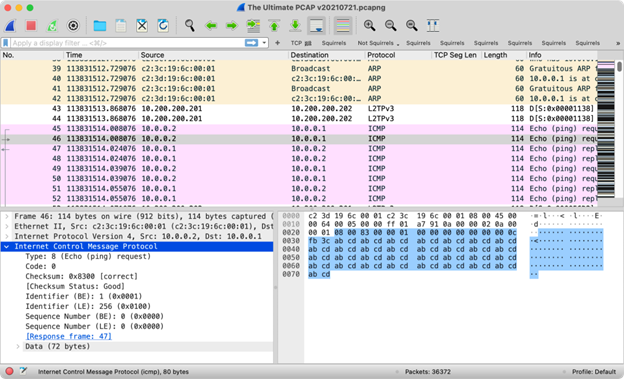
There’s a lot more to Wireshark than can be covered here. If you would like to find out more, you can find all sorts of tutorials that show you how to get the most out of it. For instance, DPI Consortium Advisory Board members Laura Chappell and Mike Pennacchi have some great videos on YouTube.
Gerald Combs is the creator and lead developer of Wireshark and the CFO of the Wireshark Foundation, a nonprofit which promotes protocol analysis education.
Check out other articles and information on our Resource page